The rise of cybercrime combined with widespread remote and hybrid working has put IT security under the spotlight. UK organisations now face threats such as phishing, ransomware and credential theft on multiple fronts, including home and public networks. In fact, recent studies show that nearly all large British businesses have suffered cyber-attacks in the past year, with many executives citing remote and hybrid workers as the main vulnerability. In this environment, business leaders are questioning whether legacy security strategies can still keep them safe.
The Role of SD-WAN in Modern Networks
SD-WAN has become the go-to solution for modern enterprise connectivity. By creating a software-defined overlay, it lets organisations use any mix of broadband, 4G/5G and even satellite links to connect offices and users, steering traffic dynamically over the best path. This delivers centralised control and better performance for SaaS and cloud applications, while cutting costs by reducing reliance on expensive MPLS lines. SD-WAN solutions typically include key security features such as IPsec encryption and traffic segmentation, providing a baseline of protection for data in transit.
Leading SD WAN providers and managed SD-WAN services further simplify the deployment. Many vendors (for instance, Cisco Viptela, Arista/VeloCloud and Fortinet) offer co-managed or fully managed SD-WAN solutions. These typically include cloud-based orchestration and pre-configured appliances, so that branches can come online quickly with zero-touch provisioning. For example, Digital Carbon’s managed SD-WAN service arrives configured for optimal performance: it runs application-aware traffic management in real time, prioritising critical apps and encrypting data across all links.
Yet while sd wan managed services and solutions provide strong network-layer protection, they mainly defend against traditional WAN problems (packet loss, congestion, MPLS cost and lack of visibility). They work well for the “tried and true” network threats such as dropped links or basic denial-of-service, but they do not catch more complex, application-level attacks. Many standalone SD-WAN setups assume that deeper security functions (like email scanning, malware sandboxing or data loss prevention) are handled by separate tools, leaving gaps in the protection of hybrid users.
The Changing Threat Landscape
The current cyber-threat landscape shows why these extra layers are needed. Sophisticated attackers now exploit application-level vulnerabilities, target cloud credentials, and craft phishing lures specifically for dispersed workforces. Malware and ransomware gangs are also increasingly probing VPNs, routers and personal devices to break into corporate networks. In the UK context, research finds that remote and hybrid workers are blamed for nearly half of recent breaches. For example, one IT survey reported that 46% of enterprises cited remote/hybrid staff as the primary source of breaches, far more than any other factor.
Traditional SD-WAN improves connectivity resilience, but it does not inspect encrypted web traffic, analyse files in transit, or block sophisticated threats by itself. In practice, much of today’s attack traffic (malicious email attachments, compromised web links, etc.) still flows through SD-WAN overlays without advanced filtering. As Palo Alto Networks observes, “Traditional SD-WANs… do improve connectivity costs and flexibility, but they also majorly lack robust security features”. In short, SD-WAN by itself cannot detect or contain many modern threats.
Secure Access Service Edge (SASE): Extending SD-WAN with Cloud Security
Given these trends, many organisations are looking to SASE (Secure Access Service Edge). As defined by Gartner, SASE “delivers converged network and security as a service capabilities, including SD-WAN, SWG, CASB, NGFW and ZTNA”. In plain terms, SASE merges the connectivity of SD-WAN with a full suite of cloud-based security services, all delivered from distributed Points of Presence (PoPs). A Network World explainer calls SASE “a network architecture that combines software-defined WAN and security functionality into a unified cloud service”.
By delivering security from the cloud edge rather than a central hub, SASE solves key latency and coverage issues. Each user or site connects to the nearest SASE node (often a global PoP) where policies and protections are applied consistently. This means advanced functions – such as malware sandboxing, SSL/TLS decryption and real-time threat intelligence feeds – can be embedded at every edge location. Data Loss Prevention (DLP) is another key piece: for example, the CASB component in SASE often includes enterprise-grade DLP controls to block sensitive data exfiltration.
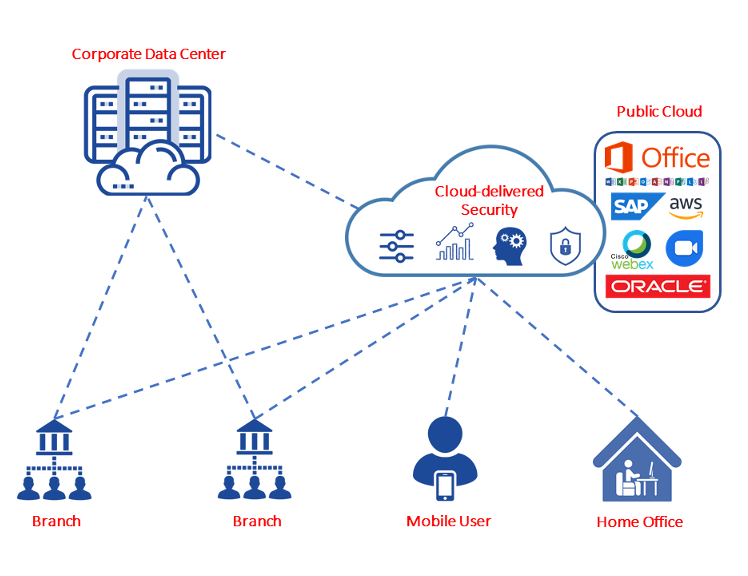
Key Benefits of SASE for Hybrid IT
-
Consistent Security Everywhere. By shifting the security perimeter to the cloud edge, SASE ensures that branch offices, home workers and even travelling employees all receive the same protections. Internet and SaaS traffic can be filtered by a secure web gateway, and uploads/downloads scanned by sandboxing engines before reaching the user. Meanwhile, Zero Trust Network Access (ZTNA) rules enforce “never trust, always verify” on every connection – checking user identity and device posture in real time. This uniform approach dramatically reduces the gaps that can occur when branch firewalls and cloud services were managed separately.
-
Reduced Complexity. A single SASE platform replaces multiple appliances. There’s no need to operate a separate VPN concentrator, web filter or on-site firewall at each location. Instead, policy management is centralised: administrators define rules once (for example, which applications remote users can access and under what conditions) and those rules cascade automatically to all edges. This dramatically cuts operational overhead and helps maintain compliance. Analysts even note that SASE “converges networking and security into a unified, cloud-delivered service,” eliminating siloed management.
-
Improved Performance. By routing traffic for cloud apps and the internet to the nearest SASE PoP, latency for remote workers often drops compared to backhauling everything through HQ. Many SASE providers also optimise link utilisation – just as SD-WAN does – but now with security inspection at the edge. In fact, UK analysts report that enterprises are already “adopting SD-WAN as part of a comprehensive SASE solution, often as a fully managed SASE service”. In practice, this means connectivity and security are delivered together from the cloud, offering both reliability and protection.
-
Adaptive, Zero-Trust Security. SASE platforms continuously update their protections based on threat intelligence and context. For example, many SASE solutions ingest live threat feeds so that newly discovered malicious IPs or domains are immediately blocked. If a user moves or a new SaaS app is added, access policies apply automatically across the entire network. This adaptability is crucial given the pace of change in cyber threats. In essence, SASE embodies zero trust by default, vetting every connection and device – exactly the kind of model the UK’s own security guidance now recommends for hybrid workforces.
Is SD-WAN Still Relevant?
Importantly, adopting SASE does not mean abandoning SD-WAN. In fact, SD-WAN remains the networking foundation within any SASE architecture. The best practice is to view SD-WAN and SASE as complementary. SD-WAN provides the secure, resilient underlay tunnels and visibility that IT teams rely on, while SASE wraps around SD-WAN to add deep threat protection and inspection. Many companies first deploy SD-WAN (often via a co-managed service) and then layer on SASE security. As ISG notes, “Because SASE rests on a framework of SD-WAN, the need for managed SD-WAN remains high”. In other words, world-class SD-WAN managed services (managed sd wan) are still critical as the base of a SASE rollout.
Some organisations may choose a single-vendor SASE platform that bundles SD-WAN. Market forecasts show this is already happening: Gartner predicts that by 2025 about 50% of new SD-WAN purchases will be part of a single-vendor SASE offering. The net effect is that SD-WAN providers and managed services firms now offer integrated SD-WAN+SASE packages, rather than selling SD-WAN and security separately. According to analysts, there is “a place for companies only offering standalone SD-WAN, but… opportunities are muted” without SASE In practice, many UK businesses opt for both – upgrading their WAN fabric (often with a managed SD-WAN service) and then implementing SASE on top.
Conclusion: A Next-Generation Approach to Secure Networking
In summary, SD-WAN alone offers many benefits for branch performance and baseline encryption, but it was never designed as a complete security solution. With cybercrime on the rise and remote work here to stay, UK IT leaders should consider SASE as a strategic extension of SD-WAN. The combination of managed SD-WAN connectivity and cloud-delivered security (SASE) provides a holistic architecture addressing both network and application threats. By converging these functions, organisations can streamline management while raising security to the level demanded by today’s hybrid environment.
If your organisation is planning its next network upgrade or security refresh, we recommend evaluating SASE alongside SD-WAN. Digital Carbon has deep experience delivering SD-WAN solutions and SASE designs for UK enterprises. Book a consultation or hands-on workshop with our team to explore how a combined SD-WAN/SASE approach could safeguard your hybrid workforce. Take the first step towards a future-ready network — schedule your workshop with Digital Carbon today and secure your organisation for the next era of work.

